It was a cool, light evening in Orlando, Florida. The night had a bunch of life happening off in the distance.
For me, it was a time of peace, and of calm.
I had just ordered an Irish Coffee, and was looking to unwind.
I bet you understand those days. Days when the board meeting was a little too fast-paced. A day when your CIO or CTO royally screwed up and it caused a near shutdown. Or maybe one in which your HR director wasn’t handling their end and you were on the phone with a lawyer all day.

“Hey, buddy!” shouted a voice too close to have to shout.
I turned, with a smile, knowing the voice all too well.
“I know it’s late, but I had a thought, and a question, before you left tomorrow morning. Okay…so our company has grown the last decade, as you know. But, but, we have a problem sharing files back and forth for upcoming projects. I’m just wondering what to avoid. Look, I know we have some older systems and methods of doing things. But, what, in your opinion, should be the things to really button down before moving onto the new year? I want to avoid the common mistakes we’re making so that we can keep growing, but not in an out-of-control way.”
“Ahhh,” I started. “Here is how…”
This type of question comes up a lot when you talk to business owners; specifically COOs, CEOs and managers at larger firms. While most websites can bombard you with the ideas of what to grab, what to look for and where to find it, there has been a lack of what to avoid when it comes to file sharing solutions for large companies.
You don’t have to track us down in an Orlando hotel’s pub to get the answer.
Today, we are going to look at enterprise-level file sharing solutions. We are going to review file sharing and data collaboration, as well as what to avoid if you are a huge company.
But, don’t let the word “enterprise” scare if you off. These are still similar, if not the exact same, issues to avoid for any size micro business, small business or corporation in this year and beyond.
What is business file sharing, in the enterprise?
Business file sharing involves the sharing of data, with many possible types, from an employee to employee, or even using an external user to internal user relationship. Business file sharing does not require physical file storage (as evidence in SaaS products), however it does use some form of notification and logging system within the application.
Enterprise file sharing does not change with smaller business sizes use and method of file sharing. Everything from financials, health records and project data can all be shared, uploaded and downloaded. Enterprise simply use two specifics in a greater scale: resources in terms of space, bandwidth and user count, and, second, security needs.
Where do we goof up with enterprise level sharing?
Humans, at our core, are not easy to transition to new things. Meaning, “if it works, it works” – so why change it?
However, this mentality, while allowing for our businesses to run effectively, will eventually yield to new technology, resource needs and security issues (like hacking, theft, etc). To operate properly, enterprises don’t need to constantly alter their business processes to operate effectively. They do, however, need to alter their tools to make their business processes most effective at the time.
Avoid using separate applications for EVERY SINGLE THING
One of the largest problems with deciding on enterprise level data sharing solutions is in the number of applications used to handle them. In 2017, we have more choices, to have less needs. However, enterprises can still have issues.
The big no-no here is in using an application for every single process in the stack. For instance, with file sharing in the past, business have turned to FTP and email. Whether these organizations were thousands of employees, or just two, both FTP file sharing and email data sharing were used.
However, there was no tracking, no reporting and no notification systems in place for these. Instead, more applications were layered on top of these applications to handle the additional needs. This turns a single application for a single business process, into three or four.
And now, time for the punchline: in enterprise formats, this would be multiplied by the employee count and outside contractors for installation and maintenance.
You can see how much time, energy and money is wasted with this method of ‘solution’ for data sharing.
The solution: Use a single product made for file sharing
In 2017, there are hundreds of products that allow for enterprise, as well as small business, to have secure and simple methods of sharing data between employees and outside users. Because these are centralized (SaaS products usually are), there is nothing to install, nor maintain. Meaning, no upgrades, no installations of update, nothing.
Avoid using BYOD & IoT without a policy
In 2017, enterprise must be aware, address and control BYOD (bring your own device) and IoT (internet of things) landscapes. Your employees likely have transitioned from taking notes during meetings on a pad and paper, to electronically recording them. The same occurs for collaborations of projects, document sharing, and even document signing.
However, many businesses do not use a BYOD policy nor an IoT policy for employees. As of 2015, Tech Pro Research reported that 72% of businesses have or are adopting BYOD in the workplace.

As well, many of these devices fall into company-owned and employee-owned. This adds an additional frustration when dealing with security, security upgrades and updates.
For example, your company allows for an employee to join your network. However, this employee accidentally visited a risky site. Their device is infected, which means that your network is infected, which means your business, other employees, clients and revenue are infected as well.
Not good…
Another example arises with company owned devices being used by employees for non-company actions. If this action results in a legal or social issue, the company could be named in any litigation or public/social concerns.
That is also not good…
The solution: implement a BYOD/IoT policy
The most simple, and often most overlooked, method of controlling BYOD use is to simply create and deploy a BYOD/IoT policy.
What goes into a BYOD policy? A BYOD policy outlines the devices used, their uses, who owns what, and how the devices get used.
- Specify each device permitted and why
- Define the services and support for the devices outlined under the BYOD policy
- Clearly define ownership of the device, ownership of the data
- Clearly define the employee exit strategy for any devices, data and access
- Outline and define the security policies for all devices
- Define what applications, websites, networks and apps are allowed or banned
- Integrate your online policy and social policy
- Define and clearly outline access controls of the employer and IT department
Defining and deploying a BYOD/IoT policy can be a difficult task depending on your industry. However, this is a process that yields security and productivity benefits that cannot be ignored.
Avoid growing the amount of uneducated employees
Education is everything. The more you know, the less issues you should have, correct?
This isn’t always the case…
Employees, at every level, fall into security gaps that create instances where data breaches can come to light.
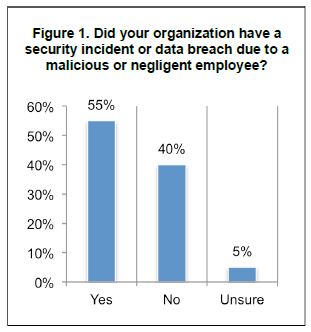
What percentage of data breaches are caused by employees?
55% of organizations having a security incident or data breach reported a malicious or negligent employee as the reason.
The more unsettling statistic from this survey is that 5% of respondents were unsure if the employees were responsible or something else. We’ll look at that later in this article.
Solution: employee training from day one, on multiple fronts
From employee start dates, until the day the employee exits your company, there should be constant training, reinforcement and auditing of security processes. Once security becomes less of a nuisance and more of a habit, this are of enterprise security will also become an invisible process.
Business security, and data security specifically, should never be thought of as a nuisance. The average total cost of a data breach is $4 million, according to a study from Security Intelligence. The global study also states that the likelihood of a material data breach involving 10,000 or more lost or stolen records in the next 24 months is at 26%.
Those numbers are a bit more than a simple nuisance.
Avoid using poor password health
Passwords have been a problem for IT staffs since computer security was a thought. The idea of a password to enter a secure system might seem small and tiny to the large deals and projects that you are working on, but those passwords keep that previously mentioned data safe. Without them, you have a secure pile of comfort, falling into the wrong hands.
With that monumental weight of password health being at issue, why is 123456 the most widely used password in 2016?
What are the most common passwords used in 2016?
- 123456
- 123456789
- qwerty
- 12345678
- 111111
- 1234567890
- 1234567
- password
- 123123
- 987654321
Unfortunately, after 20+ years of experts in security and hacking have warned billions of people about password health and password strength, this is how nearly 50% of the internet logs into their various accounts…
Solution: make your passwords stronger, harder and better
The solution for password security is simple.
- Have no maximum password length
- Have no native-language words
- Have no sequential numbers or letters
- Include all special characters
- Have high minimum password lengths (12, 16 or more)
- Don’t require constant password changes
- Force a password change on FIRST login into a system
If your password follows the above, ‘guessing’ is out of the question for a hacker. As well, dictionary attacks, brute forces and other very public intrusion methods all become lower and lower as possible successful.
Avoid a lack of tracking and logging in business processes
I could give you a ton of statistics about large-scale applications, charts concerning employee numbers and break-downs of break-points for possible intrusions based on a spectrum of different data. Or, I could just say this: no matter your company’s size, if you don’t know how something happened, you can never truly fix it.
Sounds easy, right?
Many enterprises install and maintain large business process that run. They have a task, and based on other employees or machines, these tasks are accomplished.
The problem with relying on this simple approach is that you never entirely know how you got from point A to point B.
This is what makes tracking, reporting, auditing and logging so important to the health and well-being of your brand.
But, do you adequately use these versions of monitoring and auditing? In other words, is every task, not just the most important ones, using tracking effectively to make your company even more successful.
Unfortunately, the answer is not a 100% yes.
Solution: logs, activity, reporting and audits
Digitally, we have grown as a culture. We transitioned from the stone age to the bronze age to the iron age. In more recent times, we have transitioned from the machine age, to the atomic age, to the information age.
Because of the age that we live in, we are afforded an extremely important element that allows us to constantly, and in real-time, find more and more productive approaches to the same tasks. We can more accurately (and in faster terms) track, log, audit, report, recalculate and output tasks in terms of resource usage.
However, enterprise-level companies neglect this. Results are paramount, but only if you have the data to understand the why and how.
Quick tip: tracking and reporting are requirements for most compliance and regulation standards.
This means that by not you put yourself in a tight spot.
Are you not using tracking for employee action? Are you not reporting on both normal business as well as possible intrusion? Do you not have a reporting and notification practice? Are you not in control of unedited logs of employee, ownership and outside actions?
If you answered any of these with a ‘no’, then you might be in some trouble without ever knowing it.
To wrap up, what can be done for enterprises looking for a data solution?
Business can be complicated. Dealing with data shouldn’t be.
We’ve looked at only a few items that will help to clean up your business, from the new employee, up to the seasoned board member. By avoiding these issues outlined, and using the solutions, your business in 2017 can be more secure and safe.
Do you need a simple, secure enterprise file sharing solution now?
Give PerfectShare a look. We will give you 14 days, for free. You can review our secure business file sharing platform, review our password security tools, our reporting and tracking information and more.