I had been sitting there, now for five minutes, with my head in my hands.
My palms were wet – not from the moist coughing of nervousness. They were wet from my burning eyes, swelling and exploding at the seams.
The news came like a tortured wave, falling in the distance, over and tumbling over. Then as it grew to be in front of me, staring at me, looking into the deepest parts of me because it was so close, it finally struck.
Assuming some bit of news, just the act of assumption, can be tiring. Thinking about the possibility and experiencing that anxiety can sometimes be worse than having the worst news be real.
On this day, everything was real.
It was one of the worst days of my childhood.
I was given the news, with a solemn and supportive hand on my shoulder, that one of the closest men to me was gone. And with him, a sister. And with her, a brother. In fact, that day, nearly a half dozen people in my young life were taken from me.
My palms were not drying, and my breathe was still escaping me.
“It will be ok,” my mother said, wiping my tears and holding me. Her cradling can waves of comfort, and catalyst for more sobbing.
“It was time. It was their time to go,” continued my father. His way wasn’t callousness, but concern. He was analytical, smart and direct.
“We’re sorry, my lovely son,” my mother began as she rocked me back and forth.
“But Santa just isn’t real.”
“And the the elves, mom?”
“No, not him either. Not the Easter Bunny, nor the Tooth Fairy,” she exactly stated.
Yep, that was a bad day.

What’s my point in telling you this?
Well, simply put, sometimes, in youth, the “if it’s too good to be true, then it probably is” mantra isn’t known yet. At that age, we would just as likely be excited that a prominent Nigerian prince needs our help AND we can become millionaires by helping!
But, even as adults, we are not fully hardened to this. We still are open to things being good and true. We still have what many know as blind faith in most areas of life.
And this is precisely how phishing kills business.
We, in general, assume that certain things are simply true. Phishing attempts on businesses want you to see certain things, in certain ways, to get what they want.
They do not want you to believe in Santa, but they do want you to believe in your CEO, CFO, Head of HR and Don from IT.
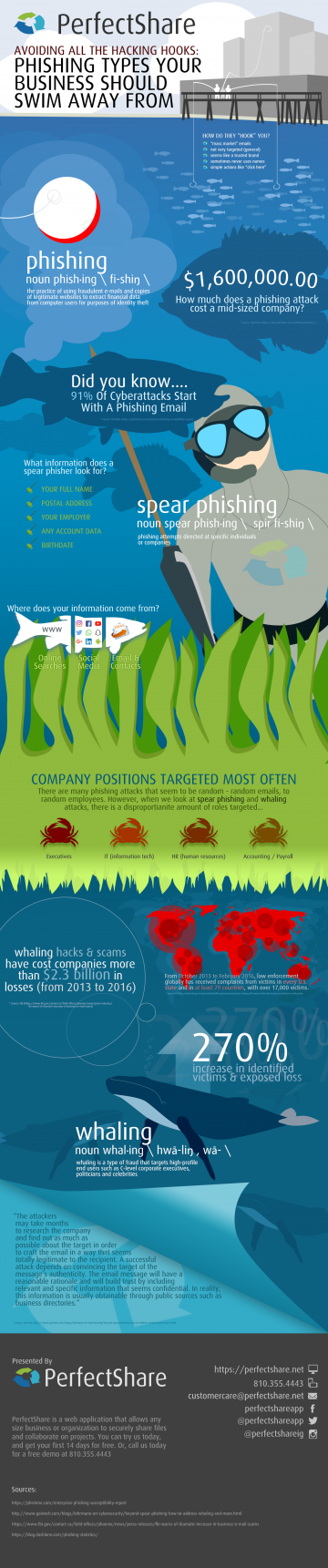
Why small businesses should take special care with phishing attacks
Phishing attacks scale. In fact, successful phishing attacks on bigger roles in a company (better known as whaling), takes time to build trust and build their version of the truth.
Notice, we say “their version of the truth”.
Imagine that happening in your adult life. Imagine that someone you have never met, could say only a few sentences in your native tongue, were able to make you believe them enough to enter your bank details, or send the W2s of all of your employees, or execute a transaction for thousands and thousands of dollars.
And yet, that is what happens, daily, to business owners and employees alike. We are sent hundreds, if not thousands, of these untrusted emails pretending to be trusted sources.
Occasionally, they work. And with the amount that can be sent, that is not good at all.
But phishing attacks don’t just scale because of their ability to send out so many to so many people. They scale in a much different way as well.
If you successfully execute a spear phishing attack or a whaling attack, you could not just receive details from a single person – you could own the personal information of the company. We aren’t just talking about names and address here… we are talking about pay stubs, social security numbers and more.
This is why phishing hacks and scams target small businesses over and over again. It is an easy way to turn a single attack in ten, one hundred or even thousands of stolen pieces of information.
What are the most common versions of phishing attacks today?
There are varying forms of phishing attacks that businesses have to contend with. They have cool names, while others are extremely clinical.
What they all share in common are the baseline practices of phishing. So, to better understand them, let us first look at what phishing is, and how companies are used in the targeting.
Rule number one – they can hit anyone, and any company.
Look at the phishing attack that hit Mattel. This attack cost the company an estimated $3,000,000 for a few minutes of emails.
Seagate was hit. Snapchat was hit. Target was hit.
Various types of phishing attacks have hit Fortune 500 and mom and pop companies alike.
So, what is phishing? And what can we do about it?
Phishing explained for your business
Phishing is the attempt to obtain sensitive information such as usernames, passwords, and credit card details (and money), often for malicious reasons, by disguising as a trustworthy entity in an electronic communication, as defined by Wikipedia.
A good example of a phishing email is one that asks you to click an apparently innocuous link. This link states the landing URL may be for Facebook or Amazon, PayPal or Bank of America. When you click the link, you are met, as expected, with a login form to sign into the service. If you enter your details, then someone other than that service or business has your details.
Do you ever get the Claim your $50 Amazon Gift Card now! Emails? What about for Walmart?
These are phishing emails.
What about notices from PayPal, or Bank of America, or CitiGroup or Stripe? They claim that your account may have been entered illegally, and they need you to verify your account…
If so, then you’ve received a phishing email.
The idea is to not specifically target a person or entity during a basic phishing attack, but to use trust factors to trigger your response (clicking the link, entering your secure login details, etc).
Here are a few more examples…
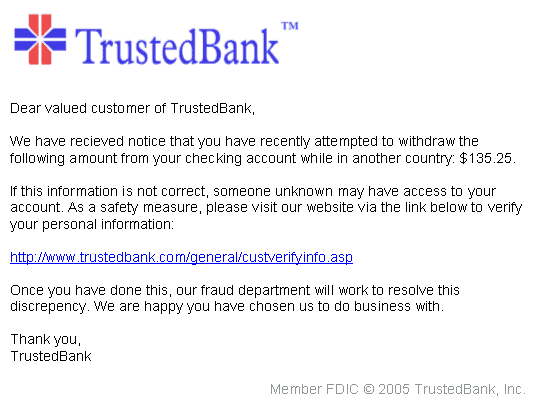 Source: Wikipedia
Source: Wikipedia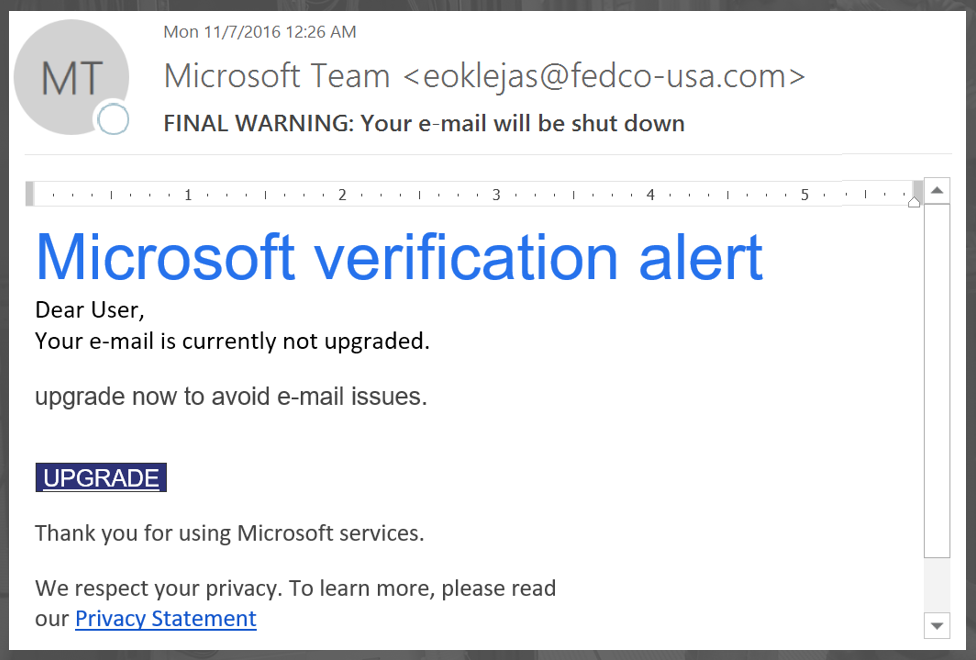 Source: Microsoft Support
Source: Microsoft Support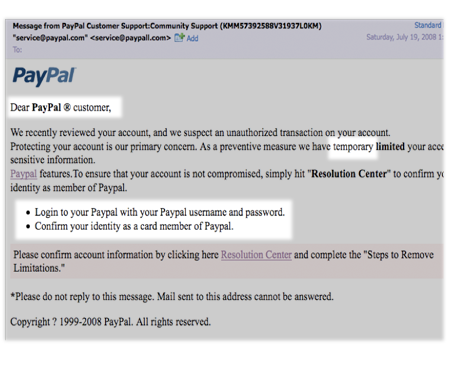 Source: PayPal
Source: PayPal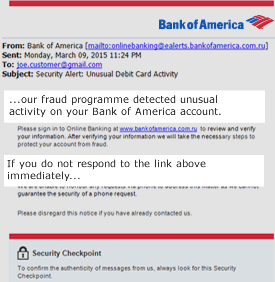 Source: Bank of America
Source: Bank of America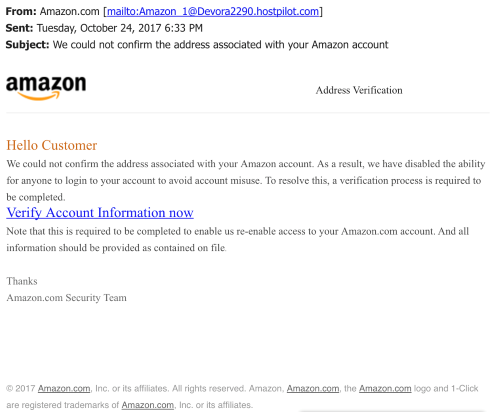 Source: Better Business Bureau (BBB)
Source: Better Business Bureau (BBB)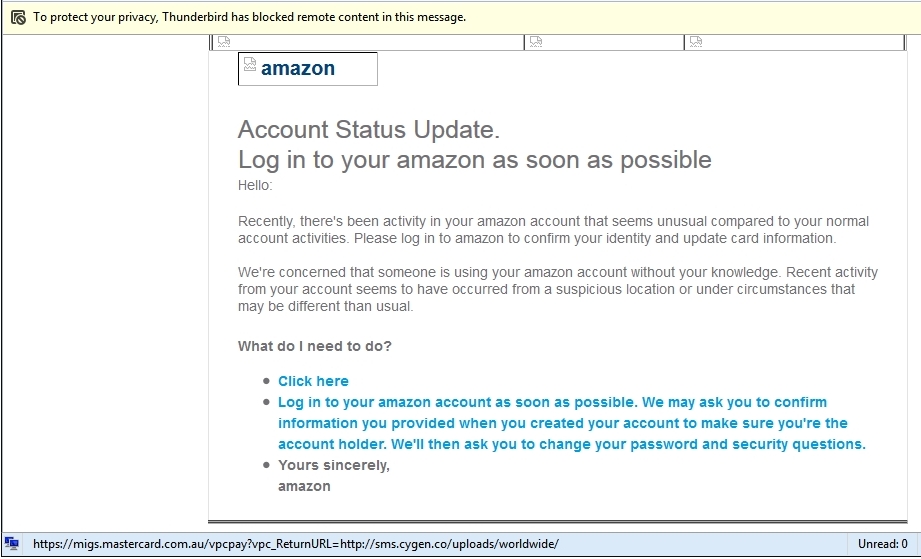 Source: Amazon
Source: Amazon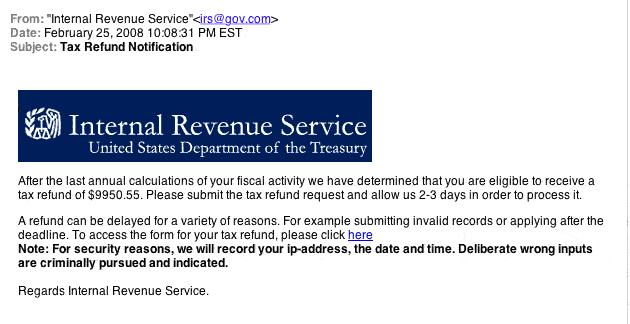 Source: Internal Revenue Service (IRS)
Source: Internal Revenue Service (IRS)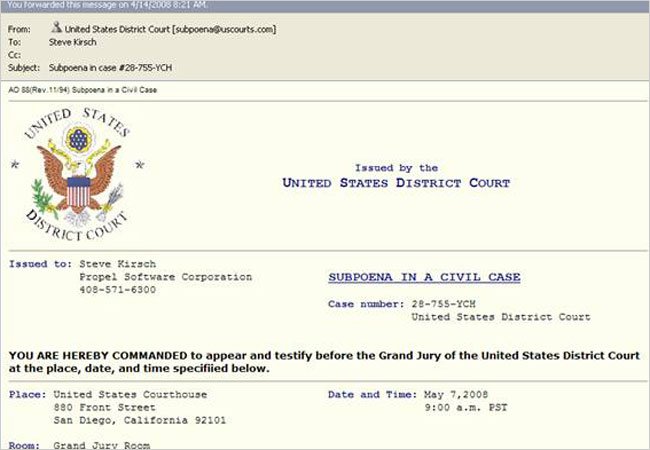 Source: New York Times
Source: New York TimesFear. Winnings. Urgency. Pain. Loss. Comfort. Hope.
As you can see, these all help to make up a basic phishing attack. Depending on the circumstance, these can all be used at different times to try to hook you and then reel you in.
But we are talking about using phishing attacks against a business, right? And for that, we need something a bit more targeted.
The basics of targeted phishing – how spear phishing actually works
Spear phishing is like phishing, but you are targeting specific people, in specific organizations. This usually requires having an idea of the person AND the organization that they work in.
From TrendMicro, “…spear phishing is a targeted form of phishing in which fraudulent emails target specific organizations in an effort to gain access to confidential information. Its tactics include impersonation, enticement and access-control bypass techniques like email filters and antivirus. The objective of spear phishing and phishing are ultimately the same—to trick a target into opening an attachment or click on a malicious embedded link.”
With spear phishing, you are also using more data. Basic phishing attacks use outside brands as trust builders. In spear phishing, knowledge of the target makes the attack work or not.
And what hidden, secure and isolated systems is this information pulled from? What hidden files are hacked to pull this data?
The answer is ridiculously simple…
It is Facebook. It is Twitter. And it is on LinkedIn.
Social media is now the default research tool for beginning a spear phishing attack.
The emails sent have a major difference from normal phishing attacks – because of the social research, these emails appear to come from a trusted coworker, schoolmate, work acquaintance or social acquaintance.
The trust moves from a large, trusted brand, to a more focused, trusted person.
The emails received are a bit different from normal phishing emails in another way. Instead of containing a link to a malicious web page, spear phishing emails will contain attachments and/or links.
Malware installation can be the goal here.
And so, the link itself allows for a payload to be installed on the target’s computer.
Whaling is a hackers big score – and here’s why
Whaling is the phishing tactic where a very specific target is selected and researched. This target is usually the head of a company, the head of a department, or the head of personnel or finance for a company. The reason for this target change is that the attacker is looking for sensitive employee information or company financial information.
Because these emails are so focused and personalized, they are difficult to detect before and after a “hit”.
One of the more recent successful whaling attacks occurred in Seagate. In this situation, the employee sent W-2 information about employees to the attackers. This affected anywhere from 50,000 to 100,000 people.
How could this happen?
The attacker researched the employee and others in their department, and matching departments. The attacker then masqueraded themselves as an executive above the employee.
Upon contact, and after establishing trust, the attacker asked for current and former W-2 information of employees. And it was sent.
This incident closely resembles an issue Snapchat had with a whaling attack. In that case, the employee was contacted with someone posing as chief executive officer. The employee was instructed to turn over employee payroll information – and it was successful.
Phishing attacks aren’t limited to these three types
As time goes on, phishing will evolve. As new phishing attacks come to light, you and your business should evaluate them and build knowledge in handling these attempts.
But you don’t know what it is, if you don’t know – right?
Let’s look at a few of the more known, and growing, variations of phishing attacks below.

Business email compromise
Business email compromise (BEC) is a hacking attack that involves impersonating an upper-level or executive employee that targets lesser employees. This attack uses altered email headers, domain names and very specific lines of “urgency” text.
While this style of phishing attack isn’t large in the small business and microbusiness world, corporations have lost over $5 billion between January 2015 to December 2016.
Clone phishing
Clone phishing involves using an exact copy of an email. This is used to mimic trust for the receiver. In essence, the email gives the receiver a false sense of trust in order to download or open attachments or links.
You’ll notice a clone phishing attack is very similar to spear phishing or whaling. What makes it different is the scale and the target. The scale is widespread, but it targets lower level employees in a particular company.
Think about a time you received a mass memo from HR, or from accounting, or even a company newsletter in your email. Now try to remember if you verified the link and/or attachment before clicking…did you?
Vishing attacks
Vishing is a phishing attacks that uses a whole other platform from email. Instead of emailing the target, the hacker or scammer uses a phone for operations.
How much more does this attack cost the attacker over email?
Technically speaking, not a lot. Most VoIP accounts could be purchased with a valid phone number for under $20 to start.
And, once again, since the trust issue of the name on your caller ID and the phone area code match, most people will pick up the phone. They are then met with a message supposedly from Apple, or Microsoft Support, or the IRS, of the local sheriff’s department, or a lawyer.
Combinations, mixology and hacking and scamming twinsies
Now, with everything said above, the point needs to be made…
All phishing attacks are the same, no matter what they are called. The attacker masks themselves as a trusted source, in order to pull any information from the target.
It makes sense, right?
Let’s see how a phishing scam works with a combined example…
The “over-the-shoulder” phishing attack
Carl Smith is a mid-level accountant working for ABC Widgets Inc. He has been with the company for 4 years. Carl has access to company records like payroll and some W2 data.
Carl has had a long week. Between the kids being sick and his vacation coming up, he’s been trying to get all the work done he can.
Today is Friday – his last Friday for a few weeks. Hawaii, after all, is looking good.
The clock ticks down. It was 4PM an hour ago, and now it is 5.
It’s almost time to leave!

*RING*
This is not what he wanted. His phone rings. The area code is his own and recognized the name.
“Carl Smith, how can I help you?”
“Hi Carl, this is Penny in HR. I was hoping to catch you before you left for Hawaii. We’ll be updating client records this next week, so I figured I could just send you the information. You can then complete them and send them back before you leave today, if possible,” she finished, with a subtle version of ‘do it now!’.
“Umm…ok. I’ll get on that Penny.”
“Thank you and have a great trip!”
Carl dreaded this. Filling out forms just was not what he wanted to do.
How did Carl’s day go after this?
Carl opens his email and notices an email from Penny in his HR department.
After opening it, he sees a basic greeting, and a document.
He opens the attachment, and fills in his data.
He then sends it back to Penny.
Carl closes his inbox, and finishes his work.
In the next hour he will close out all of his paperwork, happily shut down his computer and exit the company. After that, he will head home. He will be met by his lovely wife and kids. He’ll finish packing for his vacation. And then he’ll relax for the next 2 weeks in Hawaii.
And as for Penny from HR?
After Penny receives the attachment, she opens it.
She then records the data she gathered, and starts to investigate the next employee that she and her group can scam. She closes the spreadsheet of all of Carl’s gathered information. She also closes out the tabs opened to Carl’s Twitter feed about his vacation and his LinkedIn profile highlighting his work history and current details.
In 3-5 years, the group begins to take over Carl’s identity, opening multiple accounts. After this, they begin moving money between them and other scammed employee bank accounts. They go slow to not throw red flags.
“Penny” and her scamming group also have started to acquire enough back-end details to impersonate insurance companies, financial institutions and partners of ABC Widget Co. She’ll use Carl’s information and background as a trust flag to get in.
Then, they start their whaling attacks…
How did this all work for fast?
In this example, the employee was targeted with a few phishing attempts at the same time. But, what is interesting is that each validated the other.
When the phone rang, the name on the Caller ID plus the area code validated the person on the other end. The phone call itself was validated with details easily gained from Carl’s public social media profiles (his vacation, his work, etc). The call then validated the email he would receive. Those two validated the request for personal and sensitive information.
In each step of this umbrella phishing attack, the employee simply had to stop one time and question the details, and then verify the data.
Is this a correct number?
Is this Penny from HR? Is there a ‘Penny’ in HR?
If I’ve never met her, how does she know I’m going on vacation?
Is the sending email correctly formatted and sent?
Should I download and then upload a form with my sensitive data?
Why isn’t she asking me to stop by her office? If she can’t, why not anyone in all of HR?
Why can’t this wait until I see someone from HR face to face?
Your employees shouldn’t just question people physically in your workplace, but people virtually there. Emails, phone calls, website visits, everything is up for validation and verification.
All it takes is a second to prevent a phishing attack, but it can a lifetime and millions if not billions to recover from one.
What should your business be looking out for?
Phishing is a different form of a very common and known threat to businesses – hacking. While phishing comes in different forms, it costs a lot of money and time to correctly recover from successful attacks, just like hacking.
There are, however, four key areas to help your business prevent phishing attempts.
Education, education, education
More knowledge on a subject is always a better thing. By being able to understand what the different phishing, hacking and scamming attacks look like, you and your employees will be in a better position to neutralize them.
The best tip here is to look at everything.
Is the return email correct? Are their misspellings? Weird verbiage? Are the links pointed to unusual and unfamiliar URLs?
Start educating your employees during on-boarding and hiring, and never stop the learning.
Private profiles
Look, the fewer sources of public information on a target, the more difficult a spear phishing and whaling attack is. For nearly all social media and directories profiles, you can set them to private. This means that only ‘friends’ of the account can see the profile.
No public eyes, means no data collected for any form of phishing.
Mark external emails
Your email client should be able to handle filters. And, you, as a business owner or employee, should have a reasonable knowledge of what are the company domain is, right?
By setting a filter to mark any and all non-company emails as ‘external’, you are giving yourself a very clear visual that something is wrong with this email.
Establish verification processes
If an employee ever receives an email requesting fund transfers, financial information or any other business-critical information that isn’t typically handled by email, verify the request. You can do this from the sender via another channel such as a phone call, or, my favorite, meeting face to face with the person.
Companies should have documented processes on how these requests should be handled. Not only should employees be trained on this, but the policy should be enforced.
How can PerfectShare help your business security?
PerfectShare is a simple, secure file sharing for business platform. PerfectShare boasts branding features, activity tracking and reporting tools and full access control of your sensitive data.
If you would like to see how PerfectShare can help your business, start an account today – it’s free for 14 days! Try out the features, talk to your employees and customers and see why PerfectShare might just be your perfect solution for your business issues.
Or, call us to schedule a demo of PerfectShare at 724.510.7203 today.