You’re sitting in your office, on a chilly Thursday morning. Your content…the office isn’t Bermuda or Venice, but things are good this December day.
Looking over your newsfeed or your news app, what do you see? “Yahoo has 1 billion accounts hacked.” You tense with interest, and look further on down…
“Why OCR is aggressively enforcing HIPAA compliance ,” you read with a perked attention…
“UMass Amherst to Pay $650K HIPAA Fine” you see as you feel a bead of sweat build and roll down your forehead…
In the reading, you started to wonder, ‘Am I meeting HIPAA compliance?’
‘Am I being secure enough?’
It isn’t a fun feeling to have that kind of worry about security issues, compliance standards being met, and worse, a looming fine or hack on the horizon. However, we have a solution for you. No, it’s not a week-long stay in the Bahamas, but PerfectShare’s features will let you breathe better at night.
HIPAA and PerfectShare, together
Healthcare and other provider organizations are faced with the challenge of protecting electronic protected health information (EPHI), such as electronic health records, from various internal and external risks. To reduce risks covered entities must implement technical safeguards. PerfectShare was designed with these considers in mind.
Security standards found in the Health Insurance Portability and Accountability Act (HIPAA) are commonly known as the Security Rule. The Security Rule was adopted to implement provisions of the Health Insurance Portability and Accountability Act of 1996.
The Security Rule can be generally thought to be comprised of several topics. Some of those and organizational in nature and some are technical.
PerfectShare security features were built using these guidelines. As well, PerfectShare helps you to meet your security goals and needs time and time again.
What are they?
Access Control
Access controls provide users with rights and/or privileges to access and perform functions using information systems, applications, programs, or files. Access controls should enable authorized users to access the minimum necessary information needed to perform job functions and no more than required to fulfill that role.
Implementation specifications are associated with the Access Controls standard.
- Assign a unique username for identifying and tracking
- Emergency Access Procedure
- Automatic Logoff
- Encryption and Decryption
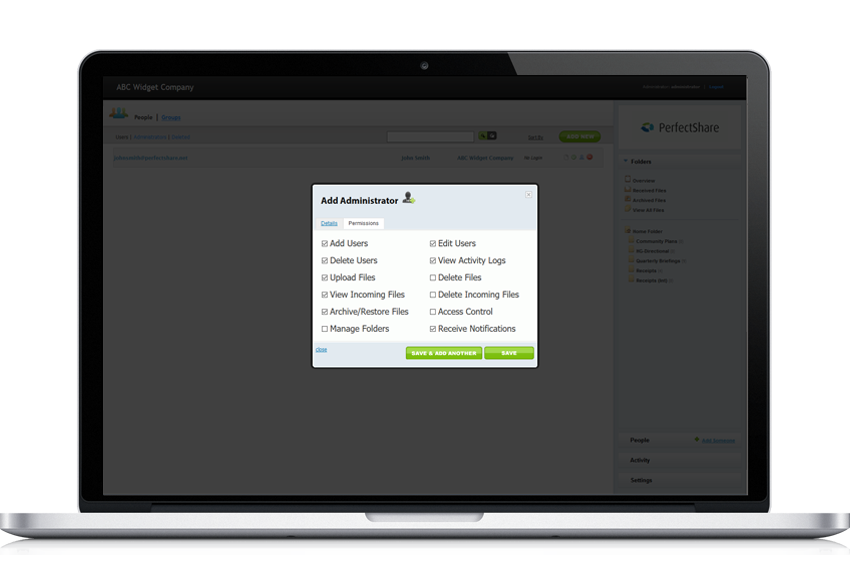
PerfectShare implements the complete protocol to insure that even the smallest of our customers can adhere to the Access Control guidelines in a cost effective manner.
Data Integrity
Integrity simply means that data or information have not been altered or destroyed in an unauthorized manner. Protecting the integrity is a primary goal of the Security Rule. The Integrity standard requires a covered entity to: “Implement policies and procedures to protect electronic protected health information from improper alteration or destruction.” PerfectShare does this through check sum validation that the data sent is also the data received and written to storage within PerfectShare.
User or Organizational Authentication
In general, authentication ensures that a person is in fact who he or she claims to be before being allowed access to data. PerfectShare accomplishes in a simple manner by requiring passwords which comply with your organizations own security policies. Your organization may set number of characters required, special characters, a combination of Upper and Lower case, and finally numbers, or a combination of all the above.
Transmission Security
Implement technical security measures to guard against unauthorized access to electronic protected health information that is being transmitted over an electronic communications network. We accomplish this by using end to end 256 bit SSL encryption to insure the integrity and privacy of the transmitted data. The secure channel is established at our end in the data center and secured to the final end point of your PC or device. This secure point to point channel insure there has been no “man in the middle” compromise.
Business Associate Contracts – Non Disclosure Agreements
The Business Associate Contracts implementation specifications state that a business associate contract must provide that the business associate will safeguard the material it receives. To this end PerfectShare has created a feature that will allow you to require business associates sign an agreement upon first login. This agreement is completely customizable by you. Once the user signs the initial agreement, it is recorded providing a permanent an audit trail. Further, a copy of the agreement is sent to both you and the signer.
Audit Trails
The Audit Controls standard requires a covered entity to implement hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use electronic protected health information.
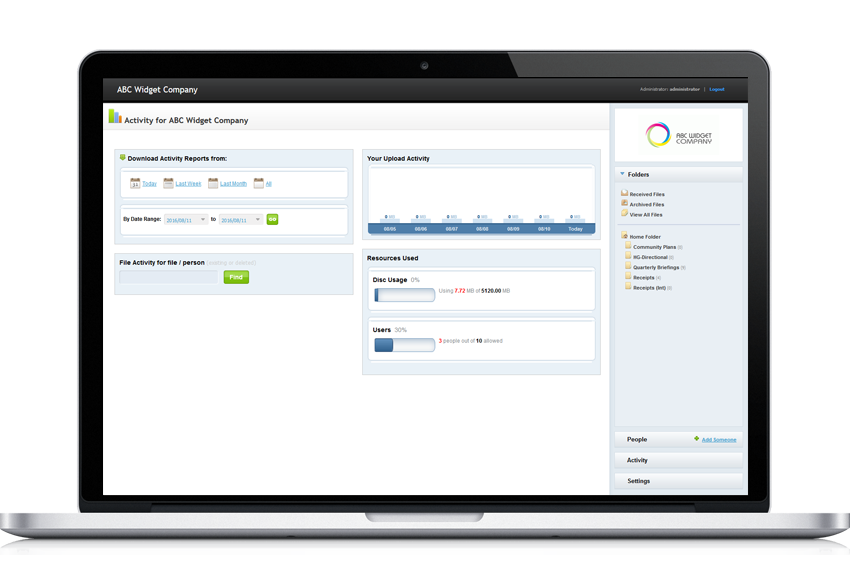
PerfectShare accomplishes this by keeping a real-time log of all user activity. This record and its associated reporting facilities are accessible to your administrators within your account. These activity logs include, login name and time, folders or files uploaded or accessed, and many other important metrics. Administrative activity is also recorded so that you own a complete audit end to end audit trail.